Complete Visibility
Eliminate Blind Spots
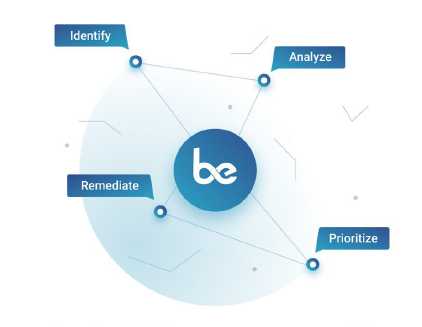
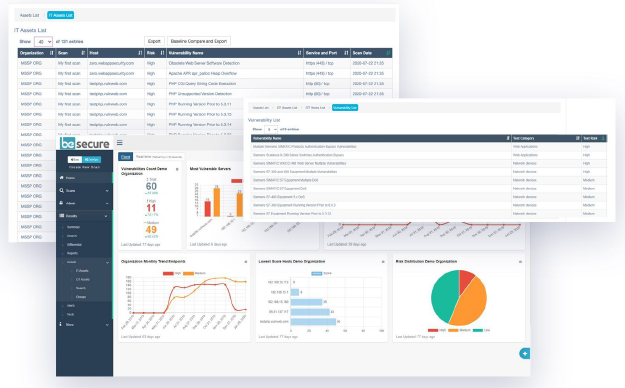
Real-time visibility across diverse networks. IT networks with computers or servers. OT (operational technology) networks with mechanical or industrial systems. Even remote working environments. Quickly classify both known and unknown assets and take control of infected or suspicious devices.
- View down to the server or device level
- Identify and manage your devices
- Converged IT and OT security
- Run HIPAA and PCI compliance scans




 Unetek
Unetek 