 The widespread use of Virtual Private Networks (VPN) to access files remotely during the Covid-19 pandemic may have created a false sense of security. Users would open their VPN client software, enter a password and gain "secure" access to the office network. But at what cost? Common problems with VPN include inefficient user interfaces, dangerous firewall pinholes, and outdated software and security.
The widespread use of Virtual Private Networks (VPN) to access files remotely during the Covid-19 pandemic may have created a false sense of security. Users would open their VPN client software, enter a password and gain "secure" access to the office network. But at what cost? Common problems with VPN include inefficient user interfaces, dangerous firewall pinholes, and outdated software and security.
There is A Better Way. Meet ZTNA.
A relatively new technology, Zero Trust Network Access (ZTNA), is a superior alternative to VPN because it is easier to deploy and use, has unmatched security, and provides actionable insight, reporting, and control. ZTNA is likely to replace legacy VPN in the not-so-distant future.
So, what is ZTNA?
Let's start with a basic analogy. Think of the key to your front door as the login credentials to your VPN. Just turn the key and you're inside with access to everything.
With ZTNA, when you walk up to your front door, a gatekeeper asks for your key, goes into the house, and retrieves selected items for you, (Only if you have proper permission).
Zero Trust.
Let's look at a more detailed explanation:
Instead of connecting to your office network via VPN, you open a connection with a dedicated server hosted in the cloud and ask for permission to access a specific, predefined folder at the office or any hosted service. The cloud server identifies who you are through multi-factor authorization and checks your device for health, giving you a trust score. If the trust score exceeds the predetermined minimum requirements, you are granted a short-term token and the cloud server retrieves the file or hosted service for you. Users never have direct access to any files or hosted applications, even websites.
Real-life example: If you say, have an accounting person logging into Bank of America, ZTNA secures the computer, authenticates the user via multi-factor authentication (MFA), ensures the policies are met, and then grants access to that website. This works with Microsoft and M365 as well. No access to Teams, OneDrive, or any hosted app, service, or website until you are authenticated on that machine.
Zero Trust.
This trust score is continuously monitored and updated using AI and if it changes, user access is immediately and automatically revoked. All administration including device permissions, user permissions, and trust score requirements are managed through a web interface also hosted in this dedicated cloud server.
What's wrong with VPN?
Plain and simple, it's security. VPN is too broad in its access. Once connected, the user has unfettered access to the entire workplace network, so the VPN is secure until it's not. Another potential issue comes up when organizations deploy VPNs and then stop paying for a support agreement. This eventually disables software patches and updates while the number of external threats continues to rise. There is a common misconception that if it's "working" it must be safe and secure.
Don't underestimate the user experience. "Good enough" is just a compromise and a VPN connection can be cluttered and finicky. Users always want a more efficient experience. Also with a hodgepodge of applications and systems, it can become confusing. In many cases, there are multiple VPN Client solutions from different vendors across an organization, resulting in support issues as users may be forced to use one app to get here, and another app to get there.
With VPNs, misconfiguration is also possible and does happen. It's Murphy's Law. Then when a problem arises, business continuity almost always wins out over security. The thinking is that it's more important to keep the business going and worry about the security risks later - a risky strategy.
When it comes to security, some organizations tend to focus a lot on remote access, but should data access over WiFi in the office be treated any differently? With WiFi, you just need a password that is usually remembered by your devices, whereas remote access with ZTNA includes token-based MFA and device posture check. So, ZTNA is not solely a remote access tool, it is perfectly suited for in-office access as well. Once implemented, ZTNA offers superior security inside and outside the office environment.
Old versus New
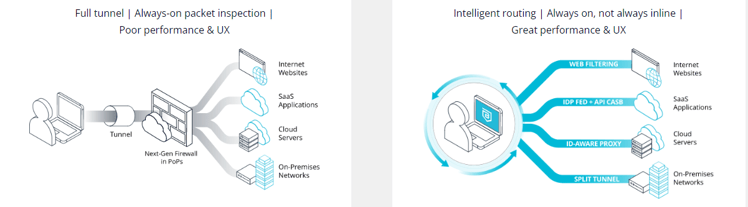
Why ZTNA is better
Security with ZTNA is twice that of VPN because users never have direct access to files or hosted services. They only have access to a proxy that has its own secure, maintained, and updated access. Even before the user gets access to this proxy, they are authenticated and their device is scanned to make sure it's healthy, current with Antivirus, and updated with the most current security patches. This security scan is not a one-time checkpoint. It's a continuous monitor of the user and the device's activities and status.
ZTNA is more efficient than legacy VPN because there is no hopping around between different apps to get to different locations. All applications are accessed from one single connection.
Deployment and management are improved because it's cloud-based with a single point of administration. There is no longer a need to remote into a user's PC or home network to install software, change settings or update permissions.
Summary
Zero Trust Network Access will replace what we know as VPN because it provides a better user experience and much-improved security. Zero trust means exactly that. The user may have the proper credentials but the data remains protected because there is never direct access to any files or hosted locations. The additional layer of security provided by continuous authentication and device posture/health checks is an added bonus. This streamlined method provides a much cleaner, quicker, and more organized experience providing users with access to the applications and files they need. These combined benefits will eventually push legacy VPN aside, making way for ZTNA as the preferred method for remote and local data access.



 Unetek
Unetek 